This is a tutorial for deploying Arch Linux in UpCloud’s cloud environment. The process described here results in a clean Arch installation with a working SSH connection. If you are new to Arch Linux, make sure to check out the official wiki pages to learn more.
The ArchWiki is one of the best Linux resources available, and it can be applied to other Linux distributions as well to some extent. Some steps described in this tutorial are directly from the ArchWiki, and links are provided for more details on the steps.
The guide assumes basic Linux understanding and a Linux environment on the client side. This is a completely manual installation, although initialization scripts are definitely a possibility to look into.
1. Deploy the image
Begin by login to your UpCloud account or getting signed up if you haven’t already.
Click the Deploy server button to open a new server configuration.
Choose your preferred Location, Plan, and Storage according to your liking. In this example, we are using the following options:
- Location DE-FRA1 in Germany
- $5 Simple plan with 1 CPU core, 1 GB memory, and 25 GB storage
Next, select the Operating System
- Open the CDROM tab
- Select the latest 64-bit Arch Linux installation CD
- Arch is a rolling release distro, so it will be fully up to date once the installation finishes
Optionals can be left as they are including the SSH keys as these cannot be added at this point and are going to be deployed manually later.
Then, change hostname and description as you wish.
Finally, click the Deploy button to launch the new server.
2. Preparations for installation
As the installation of Arch Linux consists only of working in the command line, the console connection is the place to start. The difficulty here lies in the caveats of the console connection provided. These can be circumvented with an ad-hoc SSH connection.
First, use the console connection at your UpCloud control panel with a web browser. Choose your deployed server, click on the Console tab, and Open the console connection.
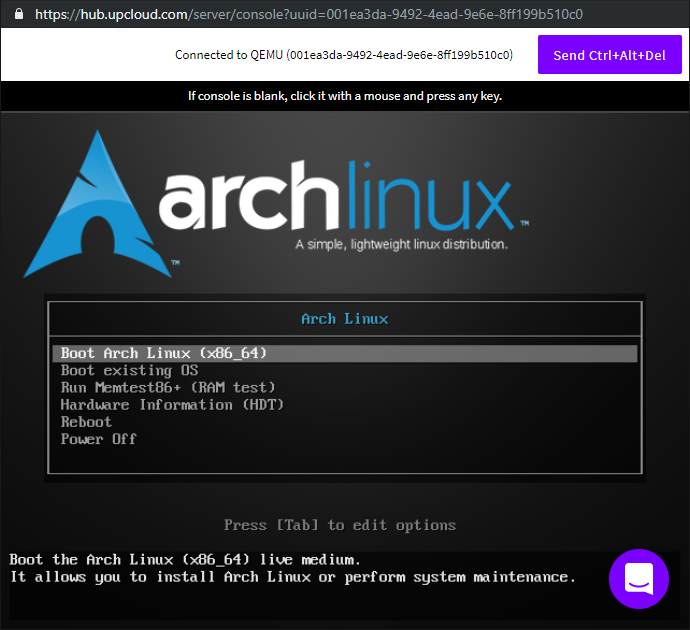
The console will open to the Arch Linux installation ISO boot menu. Press the enter key to select to Boot Arch Linux.
Once the server has fully booted up, you’ll see the usual terminal prompt.
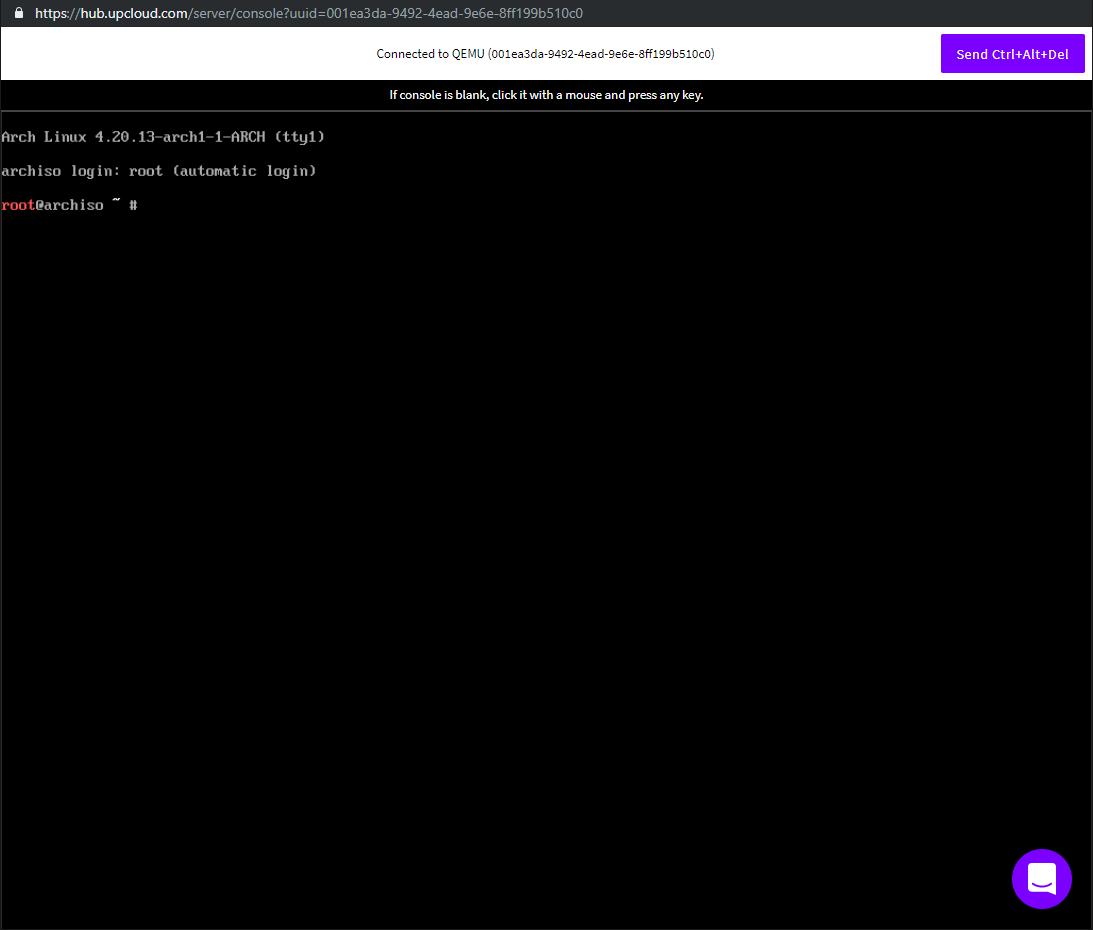
Using the web console, we are going to set up a basic SSH daemon. Enabling SSH allows us to work on the command line more easily while installing Arch using the installation CD.
To begin, lets set up a root password to prevent unauthorised connection with the following command. Enter the password you choose twice to confirm.
passwd
New password: Retype new password: passwd: password updated successfully
Next, start the SSH server.
systemctl start sshd
Then check that the SSH server is running.
systemctl status sshd
Once SSH is running, take note of your public IP address using the command below.
ip addr
The second interface and the first called ens* should have your public IPv4 address. You can also find this at your UpCloud control panel on the Servers list.
You are now ready to log in to the cloud server with SSH from your computer.
ssh root@ip-addressAccept the new host for your known_hosts list by answering yes.
If you get an error with the problem of too many authentication failures like below.
Received disconnect from ip-address port 22:2: Too many authentication failures Disconnected from ip-address port 22
Use the following command instead to attempt to authenticate properly.
ssh -o IdentitiesOnly=yes root@ip-addressOnce connected, you can continue to install the new system.
3. Installing Arch Linux
You should now be ready to install Arch. The process is quite simple but requires a little prior understanding of storage partitions. You can find more information about the following steps at the ArchWiki install guide.
Note that you need to be connected to the Arch server over SSH before proceeding. Make sure you are working on the cloud server and not inadvertently formatting your own system partitions!
First, enable the Network Time Protocol services to ensure the system clock is accurate.
timedatectl set-ntp true
Next, you’ll need to partition the storage disk.
For this example, we are going to create 3 partitions. BIOS boot partition, a root partition and a separate partition for /home.
Check the virtual hard drive label with the following command.
lsblk
In the output, you’ll see the partition like in the example below.
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT loop0 7:0 0 489.5M 1 loop /run/archiso/sfs/airootfs sr0 11:0 1 602M 0 rom /run/archiso/bootmnt vda 254:0 0 25G 0 disk
- loop0 is a squashfs which runs the installation ISO kernel
- sr0 is the ISO image mounted as a CDROM
- vda is the hard disk we want to partition
You have the following partitioning tools available on the ISO: parted, fdisk, cfdisk, and gdisk.
Feel free to choose the tool you prefer, but from these, cfdisk is probably the easiest to use. Run the partitioning tool to begin.
cfdisk
Select the gpt label type.
┌ Select label type ───┐
│ gpt │
│ dos │
│ sgi │
│ sun │
└──────────────────────┘
Partition the disk according to the following example partition scheme:
- /dev/vda1 1M BIOS boot
- /dev/vda2 8G Linux root (x86-64)
- /dev/vda3 17G Linux home
Now, create the three partitions by their size and type as outlined above.
- Select New and press enter to create a new partition
- Enter 1M as the size and press enter again
- Select Type and press enter
- Then find the partition type BIOS boot and press enter to select it
Disk: /dev/vda
Size: 25 GiB, 26843545600 bytes, 52428800 sectors
Label: gpt, identifier: DDF8E89B-550E-8840-87A9-13322F81C117
Device Start End Sectors Size Type
>> Free space 2048 52428766 52426719 25G
[ New ] [ Quit ] [ Help ] [ Write ] [ Dump ]
Create new partition from free space
Repeat the steps to create the other two partitions.
Once done, you should have three partitions as shown in the example below. Confirm the changes by selecting Write and pressing enter to save the partition table.
Disk: /dev/vda
Size: 25 GiB, 26843545600 bytes, 52428800 sectors
Label: gpt, identifier: DDF8E89B-550E-8840-87A9-13322F81C117
Device Start End Sectors Size Type
/dev/vda1 2048 4095 2048 1M BIOS boot
/dev/vda2 4096 16781311 16777216 8G Linux root (x86-64)
>> /dev/vda3 16781312 52428766 35647455 17G Linux home
┌──────────────────────────────────────────────────────────────────────────────────┐
│Partition UUID: 8124F21E-A356-F44C-A67B-A61250C472D4 │
│Partition type: Linux home (933AC7E1-2EB4-4F13-B844-0E14E2AEF915) │
└──────────────────────────────────────────────────────────────────────────────────┘
[ Delete ] [ Resize ] [ Quit ] [ Type ] [ Help ] [ Write ] [ Dump ]
Write partition table to disk (this might destroy data)
You can then quit the partitioning tool by selecting Quit and pressing enter.
Next, format the partitions and mount the filesystems with the commands below.
mkfs.vfat /dev/vda1 mkfs.ext4 /dev/vda2 mkfs.ext4 /dev/vda3 mount /dev/vda2 /mnt mkdir /mnt/home mount /dev/vda3 /mnt/home
When the partitions are set and ready, select your preferred mirror servers to install Arch Linux from by editing the /etc/pacman.d/mirrorlist file.
- The file is a simple text file with mirror server addresses
- All mirrors are enabled by default, you can back up the mirrorlist file and choose few mirrors according to your liking in close proximity
- The higher a mirror is placed in the list, the more priority it is given when downloading a package. You may want to edit the file accordingly and move the geographically closest mirrors to the top of the list.
Install the base Arch Linux and the additionally needed packages.
pacstrap /mnt base linux grub openssh nano dhcpcd
Once the installation has finished, continue below with configuring the system.
4. Configuring the system
Before the new server is ready to start on its own, you’ll need to configure a few options.
First, generate a filesystem table using the command below.
genfstab -U /mnt >> /mnt/etc/fstab
Then change into the new system using chroot.
arch-chroot /mnt
Next, set your time zone based on the region and capital city you wish, for example, using the command below.
ln -sf /usr/share/zoneinfo/Europe/Berlin /etc/localtimeYou can find the full list of time zones to select from using the following command.
timedatectl list-timezones
Configure the system clock and generate the /etc/adjtime file.
hwclock --systohc
Select your preferred locales by uncommenting the desired option in the /etc/locale.gen file. A quick way of doing so is using sed with the command below.
sed -i 's/#en_US.U/en_US.U/' /etc/locale.gen
Then generate the locales.
locale-gen
Next, create a locale.conf file with the following text.
echo "LANG=en_US.UTF-8" > /etc/locale.conf
And set your keyboard layout.
echo "KEYMAP=us" > /etc/vconsole.conf
Note that we’ll still need to make some quick configurations over the web console connection which works best with the US keyboard layout. You can change this later when SSH is up again by changing the KEYMAP variable.
Afterwards, set your system hostname as you prefer.
echo "your_hostname" > /etc/hostnameThen generate a skeleton /etc/hosts file.
cat > /etc/hosts << EOF 127.0.0.1 localhost ::1 localhost EOF
Don’t forget to set the root password now on the actual server.
passwd
Finally, install the GRUB boot loader to allow the server to start.
grub-install --target=i386-pc /dev/vda grub-mkconfig -o /boot/grub/grub.cfg
The system is now ready to boot. Exit chroot and reboot the server.
exit shutdown -h now
As we used an SSH connection, issuing a shutdown command naturally terminates the connection.
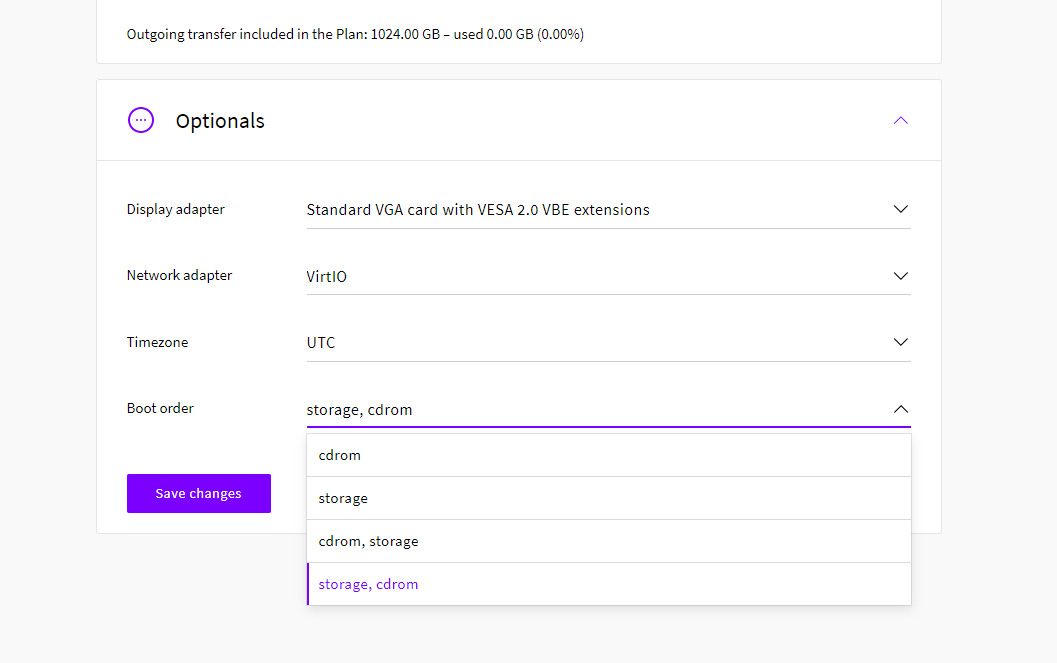
Next, to have the server boot up from the newly installed storage system you’ll need to change the boot order to select storage first. Open your cloud server settings and find the Boot order under the Optionals section at your UpCloud control panel.
Set the Boot order to storage, cdrom and shown below and then click the Save changes button.
You can then restart the server by clicking the Start button at the top right of the same page. Once your server has booted up again, you can continue with the configuration.
Note that the new system will be inaccessible via SSH for now, as the previous daemon was running on the installation ISO. See below to get this fixed.
5. Setting up SSH connection
Next, we’ll set up an SSH daemon again using the web console to be able to connect to the new machine. Go back to your UpCloud control panel.
Now is also a good time to configure a firewall. While optional at this point, it can help you protect your new server from external threats. To do this, open the UpCloud firewall page and create the following rules for SSH connections and DNS Servers on IPv4.
Incoming, default rule: DROP
Protocol Src addr Src port Tgt address Tgt port Action Notes ICMP0/IPv4 Any - Any - accept Allow echo replies in TCP/IPv4 Any Any Any 22 accept SSH connection UDP/IPv4 94.237.40.9 53 Any Any accept UpCloud DNS server UDP/IPv4 94.237.129.9 53 Any Any accept UpCloud DNS server
Outgoing, default rule: ACCEPT
TCP Any Any Any 25 drop SMTP Outbound blocked
Open a console connection to the cloud server from your UpCloud control panel and log in to the root account.
Once in, start and enable the DHCP client daemon.
systemctl enable dhcpcd systemctl start dhcpcd
Then confirm your system is getting an IP address with the ip addr command.
While connected to the console, enable root access over the SSH connection.
Make a backup copy of the sshd_config file. You should be able to use tab auto-completion to make this easier on the web console.
cp /etc/ssh/sshd_config /etc/ssh/backup.sshdconf
Next, set the PermitRootLogin yes either by editing the /etc/ssh/sshd_config file.
nano /etc/ssh/sshd_config
Alternatively, if your keymapping is working well you could use the following command to accomplish the same.
sed -i '/PermitRootLogin proh/cPermitRootLogin yes' /etc/ssh/sshd_config
Then finally enable and start the SSH daemon on the console.
systemctl enable sshd systemctl start sshd
On your local system, clear the previous entry from your known_hosts file. On the machine initiating SSH connection, a known_hosts entry was added on the installation process. The file resides at /home/user/.ssh/known_hosts. Just remove the entry associated with your server’s IP address e.g. using the command below by replacing the ip-address with your server’s public IP.
ssh-keygen -f "~/.ssh/known_hosts" -R "ip-address"Finally, connect to the cloud server using SSH.
$ ssh root@ip-addressWith the remote connection enabled, we can now further configure the server.
6. Setting up a new user and SSH authentication
You should now be connected to your new Arch server over SSH and the basic install is complete, but we are not quite done. For improved security and convenience, you should set up a new username for yourself and configure SSH keys to it.
Start by creating a new unprivileged username using the command below. Name the account as you see fit.
useradd -m usernameThen set a password for the new user.
passwd usernameNow, SSH daemon is already running but the settings allow root to log in which can be insecure. Revert the changes made to the sshd_config file by swapping it to the default config we backed up earlier.
cp /etc/ssh/backup.sshdconf /etc/ssh/sshd_config
Then, restart the SSH daemon to apply the new configuration.
systemctl restart sshd
Next, generate an SSH key pair for your regular user on your own computer. You should preferably also secure the key with a password. On Linux systems, this can be achieved with the following command.
$ ssh-keygen
Once you have created a new SSH key pair, copy over the public part to your Arch Linux server. By default, the public SSH key is saved to /home/username/.ssh/id_rsa.pub.
Then on the cloud server, change into your new user account and create the following directory.
su username
mkdir ~/.sshThe public SSH key should be saved to file at /home/username/.ssh/authorized_keys. Open a new file in a text editor, for example, by using nano and copy the public SSH key into this file.
nano ~/.ssh/authorized_keys
Then save the file and exit the editor.
Next, switch back to the root user by simply exiting your new username.
exit
You can then edit the /etc/ssh/sshd_config file according to your needs.
nano /etc/ssh/sshd_config
Here are some examples of changes you might wish to make:
- Disable the sftp subsystem if not needed by commenting out the line
- Disable password login by setting PasswordAuthentication no
- Speed up the login by setting SSH to only use IPv4 with AddressFamily inet
You can find more information about the available configuration options at the ArchWiki.
After altering the configuration, restart the SSH daemon again as the root user.
systemctl restart sshd
Then test logging in by opening a new terminal window on your own machine, and connecting with the username you created earlier.
$ ssh user@ip-address
All done!
7. Further configuration
Your Arch Linux server is now fully installed with a working SSH connection. However, the installation is very basic, and you probably want to install more programs. For example, there is currently no firewall configured and even the sudo package will need to be installed and configured separately.
Individual packages can be installed with the command below.
pacman -S packageRefer to the ArchWiki for details on packages.
Full system upgrade is done using the following command.
pacman -Suy
Since Arch pulls the latest packages during the system install, there is likely nothing to do for the moment, but remember to periodically check for updates or configure the server to do so automatically.
Note that while most upgrades can be installed without restarting the server, you should still perform a reboot after any updates to the kernel.
Additionally, if your server ever ends in an inoperable state, you can use the install CDROM as rescue media by changing the boot order again to cdrom, storage and restarting your Arch Linux server.
Testing notes
After rebooting the system via SSH connection with reboot as the root user, it might take a minute until the server accepts SSH connections again. Booting itself is really fast, but the SSH daemon can take time to fully start.
If SSH fails to connect after rebooting, logging in as any user via the web browser console connection should solve the issue and allow you to connect using SSH.

tqre
The slow startup of SSH daemon is apparently due to low entropy on cloud machines. The systemd-random-seed.service takes quite a time until enough entropy is gathered for the random number generator.
The virtual machines in UpCloud do support a certain kernel option to speed this process.
cat /proc/cpuinfo | grep rdrand
edit /etc/default/grub:
GRUB_CMDLINE_LINUX_DEFAULT=”quiet splash random.trust_cpu=on”
grub-mkconfig -o /boot/grub/grub.cfg
cat /proc/cpuinfo | grep rdrand
There was some concern for security issues about this kernel option.
Detailed explanation can be found here:
https://askubuntu.com/questions/1070433/will-ubuntu-enable-random-trust-cpu-in-the-kernel-and-what-would-be-the-effect
https://wiki.debian.org/BoottimeEntropyStarvation
The kernel option can actually be used with any linux distribution to get faster ssh access after boot.
Janne Ruostemaa
Hi there, very interesting, thanks for the comment!
Tuomo Kuure [tqre]
The current dhcpcd (8.1.1-1) package on Arch is having problems, I got max 2 days of uptime, and the daemon just failed at some point. May users are experiencing this atm.
https://bbs.archlinux.org/viewtopic.php?id=250397
https://wiki.archlinux.org/index.php/Systemd-networkd
I made use of systemd-networkd to configure the network. This systemd service is meant for public interface. Make sure you know your public IP/netmask and the default outgoing route for your hosting area. The DNS servers mentioned here are UpCloud DNS servers.
Disable and stop dhcpcd before starting systemd-networkd.
# systemctl disable dhcpcd
# systemctl stop dhcpcd
To check your current numbers:
$ ip address
$ ip route | grep default
systemd enable systemd-networkd
/etc/systemd/network/cat 20-public-ipv4.network
[Match]
Name=<public network interface>
[Network]
Address=<your public ip>/<netmask>
Gateway=<default gateway>
DNS=94.237.127.9
DNS=94.237.40.9
Disable and stop dhcpcd before starting systemd-networkd.
# systemctl disable dhcpcd
# systemctl stop dhcpcd
# systemctl enable systemd-networkd
# systemctl start systemd-networkd
Issuing a reboot command on the server with the aforementioned cpu-rdrand brings the system back up and accessible in about 10 seconds now.