A common problem with server networking is that DNS (Domain Name Service) queries get blocked by a firewall. This may result in long connection establishment times with services, such as inbound SSH, resolving reverse hostnames. It can also prevent establishing outbound connections using DNS names instead of IP addresses like with operating system updates.
Configuring your firewall for DNS server queries
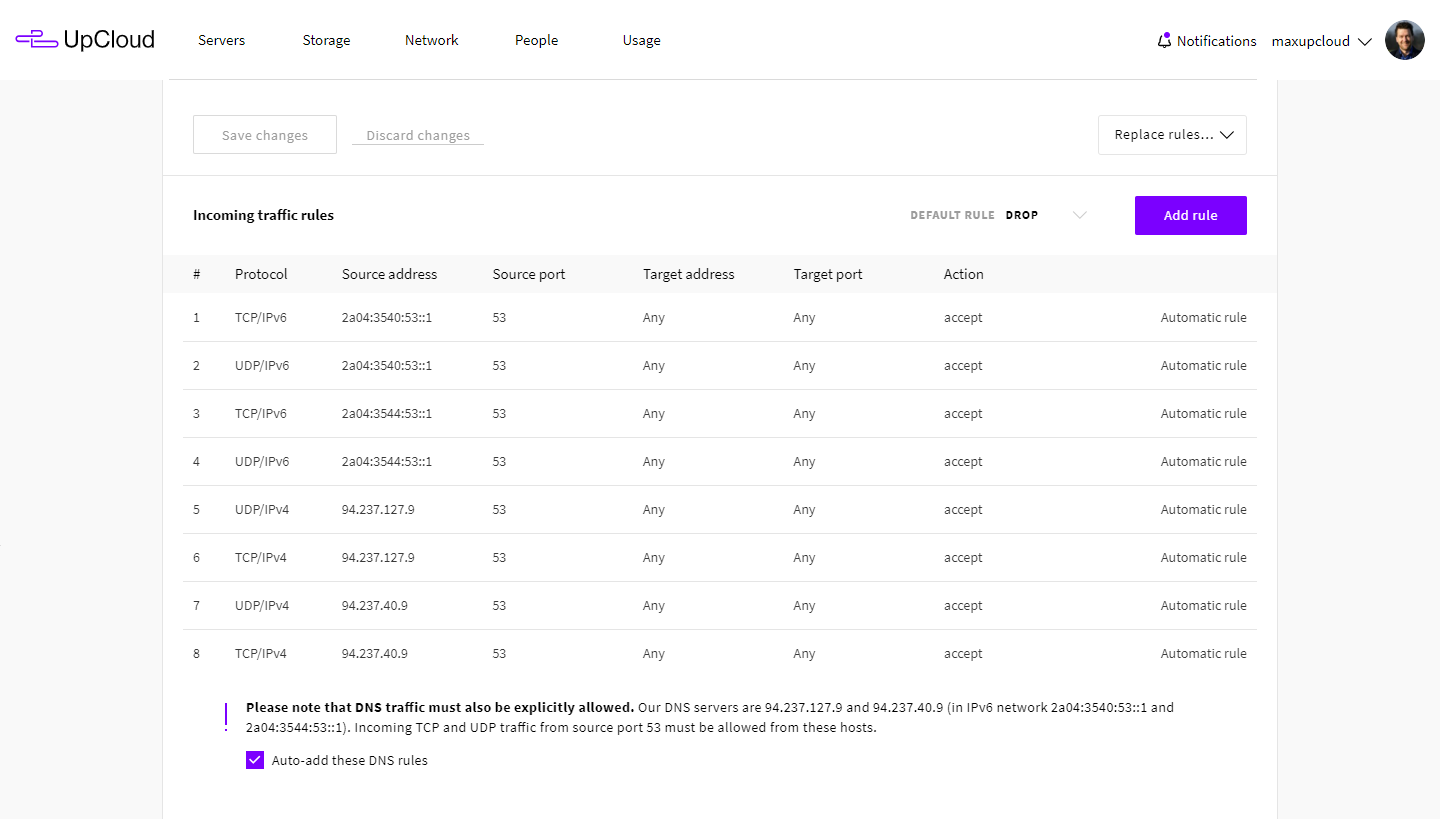
The UpCloud firewall service can be configured by using either the UpCloud Control Panel or the API. Many users also choose to run their own firewalls inside their servers such as iptables on Linux. In both cases, the DNS queries must be explicitly allowed by the firewall to have name-resolving work.
All DNS resolvers at UpCloud have the same IP addresses regardless of the availability zone. This makes it easy to copy firewall rules from one server to another or templatize firewall rules. The DNS servers are provided automatically by the DHCP protocol and there should be no need for manual configurations in the operating system, except for the DNS firewall rules.
The UpCloud DNS resolver IPv4 addresses are:
- 94.237.127.9
- 94.237.40.9
If your server has a public IPv6 address, you can also use IPv6 with the following servers:
- 2a04:3540:53::1
- 2a04:3544:53::1
The basic firewall rule for allowing DNS queries is to permit inbound UDP and TCP traffic from port 53 to any port from the DNS IP addresses. While the DNS server has traditionally worked only with UDP there are several recent additions like DNSSEC and SPF which might also require TCP connections to be allowed – otherwise, some of the queries might not go through.
You can create all required DNS firewall rules with one click by enabling the Auto-add DNS rules at your server firewall settings and then clicking the Save changes button.
Running your own DNS servers
It is also possible to use your cloud servers to provide your own DNS, which could be used as the authoritative name server for your domain. For best redundancy, it is strongly recommended that you have at least two different authoritative name servers in different locations. For example, one in our Amsterdam zone and another in Chicago.
There are several DNS server software available with the most common open source variants used with Linux being BIND, PowerDNS and djbdns. The exact configuration for each of them is outside of the scope of this article, but you can find many excellent tutorials on the Internet, starting with the documentation for the specific DNS software.
If you choose to set up your own name server, it is paramount to make sure that the server is not a so-called open resolver. These are frequently scanned and exploited by DDoS attacks against third-party targets. The key rule is to only serve replies to queries regarding your own domains, which the DNS is authoritative for. Recursion should only be allowed from localhost.
Running your own nameserver will require additional firewall settings as you must also enable inbound DNS queries. In other words, allow UDP and TCP protocol from any address to port 53 in your firewall rules.
arjun
sir if open dns recursive vulnerability occur on port 53 what should we do on that time if we also have utm firewall . Kindly suggest
Janne Ruostemaa
Hi Arjun, we’d recommend you limit access to your DNS server to only your own servers and devices according to their IP address or network. This can be done either at the UpCloud Firewall service or using any software firewall running on your DNS server.