This guide will help you install and get started with Matrix and its reference home server Synapse. The instructions and example commands in this guide will help you set up Matrix Synapse on a cloud server running CentOS 8, Debian 10, or Ubuntu 18
What is Matrix?
Matrix is an open standard for decentralised communication, which securely distributes persistent chatrooms over an open federation of servers preventing any single points of control or failure.
Matrix provides simple HTTP APIs and open-source reference implementations to create a common fabric to interconnect existing communication islands. Some of the use cases include creating and managing fully distributed conversations, enabling WebRTC VoIP and video calls using Matrix signalling, and synchronising history across all clients in real time.
1. Deploy a cloud server
If you have not already registered with UpCloud, you should begin here to get started with $25 in credits when you sign up today.
Once you have signed up, log into your UpCloud Control Panel and deploy a server.
Synapse requires a POSIX-compliant system, such as the aforementioned Linux distributions, Python 3.6 or newer installed, and at least 1GB of free RAM to be able to join large public rooms such as the #matrix:matrix.org.
Deploy a new cloud instance for hosting the Matrix home server using one of the tested Linux operating systems to an availability zone of your choosing. You can find in-depth instructions on all of the configuration options in the guide for how to deploy a server.
2. Installing prerequisites
When you have a server up and running, use the commands below appropriate to your system to install the required packages and libraries.
For Ubuntu 18 and Debian 10 systems, install the prerequisites with the following command.
sudo apt-get install build-essential python3-dev libffi-dev python-pip python-setuptools sqlite3 libssl-dev python-virtualenv libjpeg-dev libxslt1-dev
Ubuntu 20 needs a couple of newer packages so use this command instead.
sudo apt-get install build-essential python3-dev libffi-dev python3-pip python-setuptools sqlite3 libssl-dev python3-virtualenv libjpeg-dev libxslt1-dev
On CentOS 8, you can fulfil the requirements with the installs below. You will also need to enable access to the required ports and services at the firewall.
sudo dnf install libtiff-devel libjpeg-devel libzip-devel freetype-devel lcms2 libwebp-devel tcl-devel tk-devel redhat-rpm-config python36 virtualenv libffi-devel openssl-devel sudo dnf group install "Development Tools" sudo firewall-cmd --permanent --add-service http sudo firewall-cmd --permanent --add-service https sudo firewall-cmd --permanent --add-port=8448/tcp sudo firewall-cmd --reload
With the prerequisites sorted, you can continue installing Synapse.
3. Installing Synapse home server
Synapse is the Matrix reference implementation of a “home server” written by the Matrix core development team. It is intended as a showcase of the Matrix concept to demonstrate the spec in the context of a codebase. It lets you easily run your own home server and generally helps to bootstrap the Matrix ecosystem.
The home servers are used as an access point for clients to connect to the Matrix network. They store the user’s personal chat history and account information in a similar fashion as an IMAP/SMTP server would. Like email, you can run your own Matrix home server to keep personal control and ownership of your communications and history or use one of the hosted Matrix services. Matrix has no single point of control or mandatory service provider.
To prepare the system, set up a new virtual environment under ~/synapse using the commands below or choose a different directory by replacing the ~/synapse in the commands with the folder you wish to store the server files.
mkdir -p ~/synapse virtualenv -p python3 ~/synapse/env source ~/synapse/env/bin/activate
Check that the following packages are installed and up to date.
pip install --upgrade pip virtualenv six packaging appdirs
Then use pip to install and upgrade the setup tools as well as the Synapse server itself.
pip install --upgrade setuptools pip install matrix-synapse
This installs the Synapse home server along with its libraries.
If you run into problems installing the Synapse home server, Matrix has outlined some helpful troubleshooting tips on the Synapse GitHub page.
4. Configuring Synapse
Before Synapse can be started, you will need to generate a configuration file that defines the server settings.
Run the following commands in your Synapse virtual environment. Replace the server name matrix.example.com with your own domain, but note that the name cannot be changed later without reinstalling the home server. Also, choose whether you wish to allow Synapse to report statistics by entering either --report-stats=yes or no.
source ~/synapse/env/bin/activate pip install -U matrix-synapse cd ~/synapse python -m synapse.app.homeserver --server-name matrix.example.com --config-path homeserver.yaml --generate-config --report-stats=yes|no
A config file has been generated in 'homeserver.yaml' for server name 'matrix.example.com'. Please review this file and customise it to your needs.Once Synapse has finished generating the required settings, you should see a confirmation like in the example output above.
5. Enabling TLS
Matrix Synapse now requires TLS enabled by default to allow the server to be used securely. The easiest way to configure TLS is to obtain SSL certificates from a trusted Certificate Authority such as Let’s Encrypt.
Let’s Encrypt’s Certbot client is primarily distributed via Snap packages. Check below the instructions for installing Snap and Certbot client for your operating system.
The OS templates for Ubuntu 18 and 20 on UpCloud have Snap installed by default. Simply check that Snap is at its latest version and then use Snap to install Certbot.
sudo snap install core; sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot
For Debian 10, install Snap first, then Certbot.
sudo apt-get install snapd -y sudo snap install core; sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot
On CentOS 8 systems, you will first need to install the Extra Packages for Enterprise Linux (EPEL), followed by Snap and then Certbot itself.
sudo dnf install -y epel-release sudo dnf install -y snapd sudo snap install core; sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot
You’ll also need to have a web server available for Certbot to use for validating the certificate. Install nginx using the instructions below according to your operating system.
On Debian and Ubuntu systems, simply run the following command.
sudo apt-get install nginx
Nginx for CentOS 8 is also installed from the Extra Packages for Enterprise Linux (EPEL) which we already did for Certbot so just install Nginx with the command below.
sudo dnf install nginx
With the Certbot client and Nginx installed, you can obtain certificates using the certonly command together with the --nginx plugin. Include at least one domain name by replacing the matrix.example.com with yours.
Then use the Certbot client as shown in the example below.
sudo certbot certonly --nginx -d matrix.example.comThe command starts an interactive configuration script that asks a couple of questions to help with managing certificates.
- On the first installation on any specific host, you’ll need to enter a contact email.
- Then go through the Let’s Encrypt Terms of Service and select Agree if you accept the terms and wish to use the service.
- Choose whether you wish to share your email address with the Electronic Frontier Foundation (EFF) for updates on their work.
If the client was successful at obtaining a certificate you can find a confirmation and certificate expiration date at the end of the client output.
In case you are having problems with the client, make sure you are trying to register a domain or subdomain that currently resolves to your server as DNS configurations might take a moment to propagate. Also, check that you are running the command with admin privileges.
When the certificates have been issued successfully, you’ll need to enable them for the Synapse home server.
You can find out more about the Let’s Encrypt client including how to automate the certificate renewal in our article on how to install Let’s Encrypt on nginx.
6. Configuring reverse proxy with nginx
Matrix recommends setting up a reverse proxy, such as nginx, Apache or HAProxy, in front of your Synapse server. This is intended to simplify client connections by allowing Matrix to use the common HTTPS port 443 while keeping the server-to-server connections at port 8448.
Change the default home server configuration to only listen to the localhost address for port 8008. Open the homeserver.yaml file for editing.
nano ~/synapse/homeserver.yaml
Find the following segment and set the bind only to the address 127.0.0.1 and check that the forward flag is set to true as shown below. You can leave the rest as is, we’ll terminate the SSL at the proxy so Matrix does not need to worry about TLS settings.
- port: 8008
tls: false
bind_addresses: ['127.0.0.1']
type: http
x_forwarded: true
Save the file and exit.
Next, enable nginx to act as the reverse proxy by creating a configuration file for the proxy functionality.
sudo nano /etc/nginx/conf.d/matrix.conf
Then enter the following to enable the proxy with SSL termination. Replace the matrix.example.com with your domain in the server name. The certificates issued by Let’s Encrypt are saved under the directory indicated in the Certbot output, usually under /etc/letsencrypt/live/. Again, replace the matrix.example.com with the domain name the certificates were issued for.
server {
listen 80;
listen [::]:80;
server_name matrix.example.com;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
listen [::]:443 ssl;
server_name matrix.example.com;
ssl on;
ssl_certificate /etc/letsencrypt/live/matrix.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/matrix.example.com/privkey.pem;
location / {
proxy_pass http://localhost:8008;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
server {
listen 8448 ssl default_server;
listen [::]:8448 ssl default_server;
server_name matrix.example.com;
ssl on;
ssl_certificate /etc/letsencrypt/live/matrix.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/matrix.example.com/privkey.pem;
location / {
proxy_pass http://localhost:8008;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
The above nginx configuration includes three parts to help make using your Matrix Synapse home server as easy as possible. It listens for secure connections as ports 443 for HTTPS and 8448 for Matrix federation server-to-server communication. Connections to the insecure HTTP port 80 are redirected to use HTTPS instead.
Once you’re done, save the file and exit the editor.
Then start and enable nginx.
sudo systemctl restart nginx sudo systemctl enable nginx
That’s all you need for configuring a Synapse home server. Continue below to start the server and create your first user.
7. Registering a new user
Now that Synapse is installed, you should add a new user as an admin to be able to configure chat rooms and web client settings. First, make sure you are in the home server virtual environment and start the server.
cd ~/synapse source env/bin/activate synctl start
Then register a new user to the localhost.
register_new_matrix_user -c homeserver.yaml http://localhost:8008
This starts an interactive user configuration. Enter the desired username and password, and then select yes to enable administration privileges.
New user localpart [root]: username Password: password Confirm password: password Make admin [no]: yes|no Sending registration request... Success.
That is it, you should now be able to log into your Synapse home server with the user credentials you just created.
8. Logging into Matrix
Users have the ability to connect to a Matric home server using one or more Matrix clients. First, verify that the Matrix server is running and reachable by opening your domain on a web browser.
https://matrix.example.comYou should see a page such as the one below.

The home server doesn’t include a Matrix client by default but you can use the Riot web client. It has a polished and easy-to-use user interface, and after installing trusted certificates using Let’s Encrypt, you can connect to your home server using a public client such as Riot.
Go to the following URL on your web browser.
https://riot.im/app/#/login
You should see a sign-in page like in the example picture below. First, click the change link to select to use your custom Matrix server.
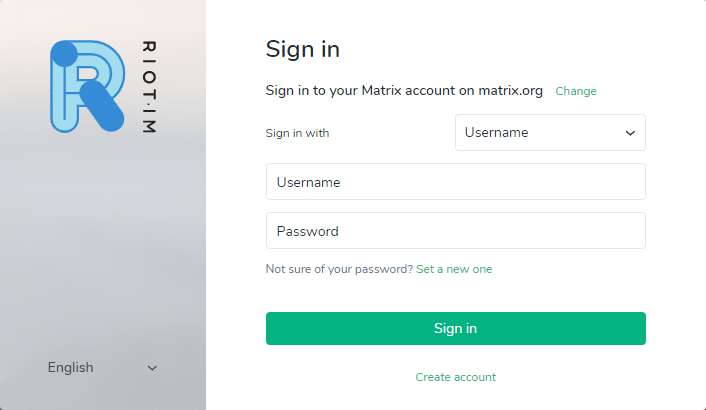
Enter your Matrix server domain name as your home server URL and click the Next button.
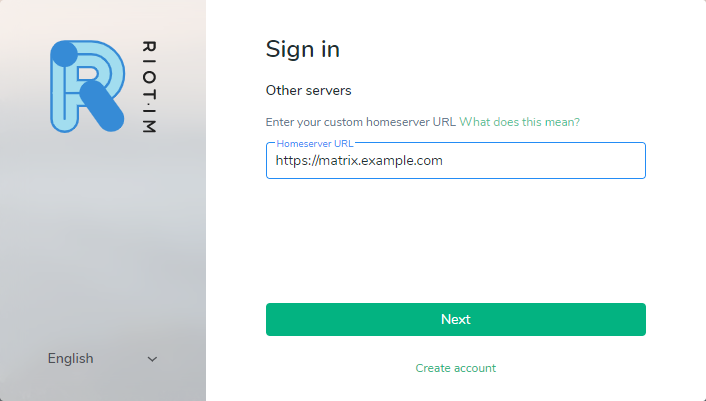
Riot will then make a quick connection check to your cloud server. If you see an error message, check your server domain and that you entered it using HTTPS.
Then sign in with the username and password you just created in the previous section for your own home server.
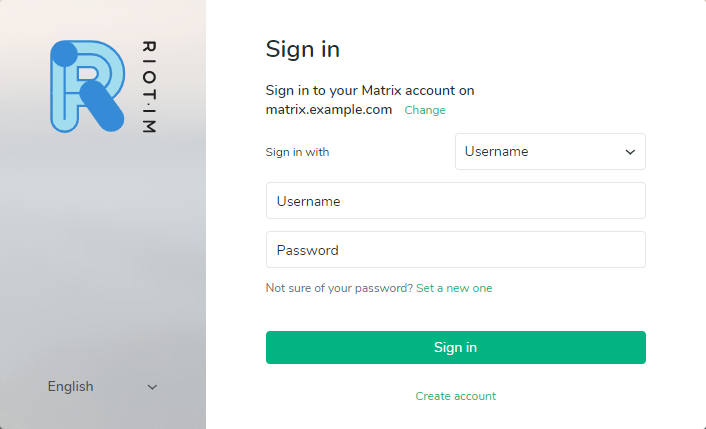
The Riot web app is a convenient way of testing your custom Matrix Synapse server but it’s definitely not the only client available. Other client applications can be found on the Matrix documentation page.
9. Creating a room
Next, you might wish to create a new room. In Matrix, everything happens in rooms which are distributed and do not exist on any single server. Rooms can be identified and located using aliases such as #matrix:matrix.org or #test:localhost:8008.
Click the plus icon to the left of the Rooms list of the Riot web client.
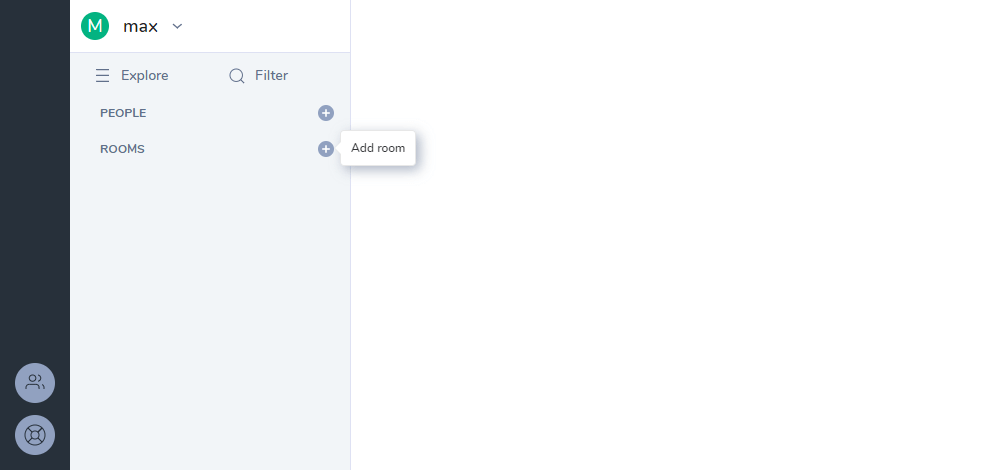
Give your room a name, and with the Synapse client, you can also make the room public if you wish.
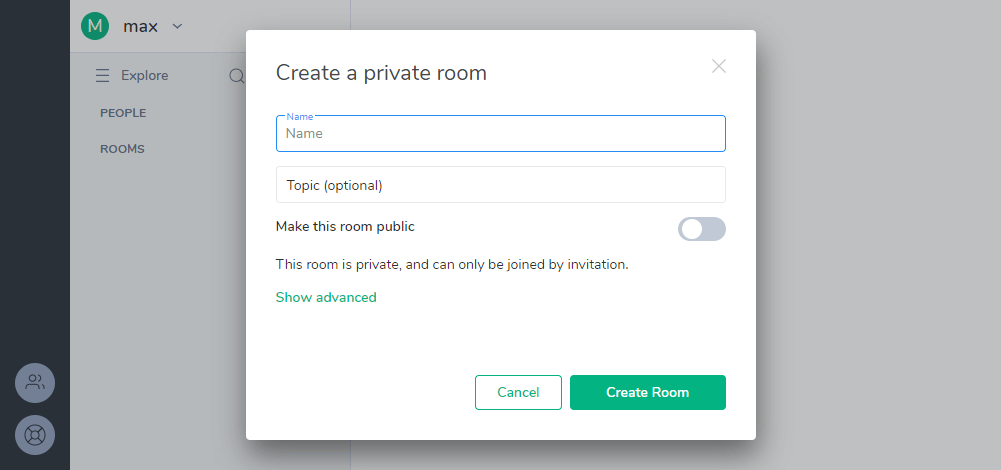
Then hit enter to save the name and join the new room.
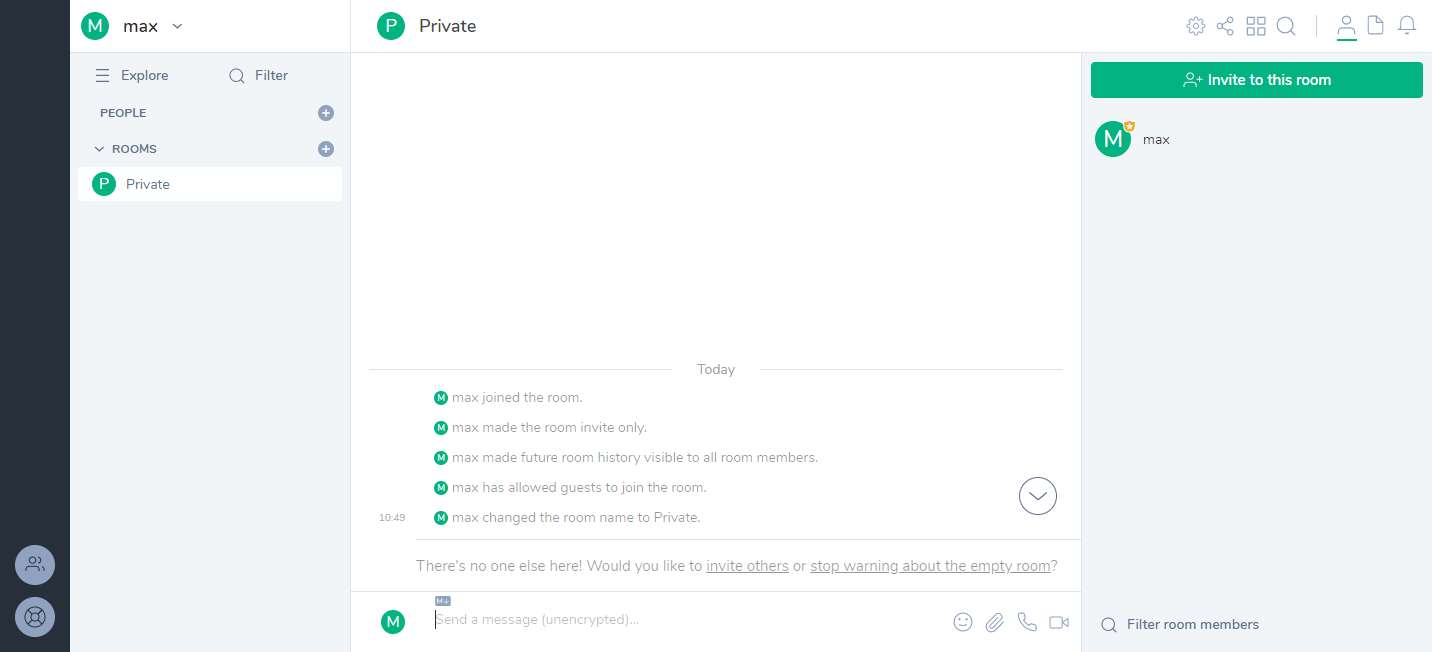
The rooms can be used just as any communication channel, but Matrix is intended to be much more capable than a simple text chat. The basic implementation of the Synapse home server and web client are just examples of how the Matrix network can be utilised. There are already a number of other options for home servers with many different use cases. You can find more publicly available application servers in the Matrix projects documentation.
All done!
Congratulations, you have now successfully deployed and configured your first Matrix home server using Synapse.
If you would like to try out different clients, Weechat Matrix plugin allows logging in even on the command line, while Riot is also available on Android and iOS. Alternatively, those with the technical know-how can always write their own client using one of the Matrix SDKs.
Matrix presents a tonne of potential for secure communication for anything from group chat rooms, VoIP and video calls, to the exchange of persistent data between devices and services in the Internet of Things. Feel free to experiment with the existing servers and clients or begin developing your own!

Jonatan
Thank you for this guide!
It was really helpful, even though I ran Nginx in a way that didn’t fit the guide it was easy enouhg to follow through.
Sami Olmari
Soon with the Synapse 1 SSL-certificates is required, not optional. So this guide needs at the least changing the part 6 wording.
Source: https://github.com/matrix-org/synapse/blob/master/docs/MSC1711_certificates_FAQ.md
Janne Ruostemaa
Hi Sami, thanks for the comment, we’ll get the guide updated to reflect the new requirement.
Kevin
Hey Janne,
this Tutorial is not up to date due the python change from 2.7 to 3.5 in synapse…
could you please update this awesome guide?
ty
Janne Ruostemaa
Hi Kevin, thanks for the comment. The guide is in need of an update and we’ll get on it soon!
Rainer
Thanks for this guide! Everything worked immediately.
LBI
On a Centos minimal install install you will need to add
sudo yum -y install gcc gcc-c++ kernel-devel
sudo yum install python36 python36-devel python36-libs python36-tools
sudo yum -y install python-devel libxslt-devel libffi-devel openssl-devel
Janne Ruostemaa
Hi there, thanks for the comment, good to know to those running a leaner CentOS install.
Duc Nguyen
Hi Jannie.
Thanks for the guide. It worked for me. But I cannot call to other people if they are using different internet, everything works fine if we use same wifi. Do you have any suggestions?
Janne Ruostemaa
Hi Duc, thanks for the comment. As for your problem, being on the same WiFi network should not matter as long as everyone is able to join the same room. Assuming you installed Matrix on a local machine which would prevent others from joining it from outside your local network. I would recommend deploying Matrix on a cloud server which will be accessible from anywhere.
monemacu
Thanks for this great tutorial!
I followed all the steps correctly, the server seems to be running in terminal just fine.
But, the subdomain that was used is still not working on riot, also does not show any matrix files as shown in Step 8. Logging into Matrix
I have no idea what to do, kindly help me out with domain configuration!
Janne Ruostemaa
Hi there, thanks for the question. You would need to have an A record pointing your domain name to the server’s IP address. The actual process of doing this depends on your domain registrar but we’ve got some general tips for managing DNS records. If you’ve already created the A record, then it’s just a matter of time for the record to propagate onto other DNS servers and become available on Matrix network.
monemacu
Thanks for your quick response!
Issue was solved by re-configuring TLS Step 5
Step 6: removing any app/process on port 80
Then, restarting nginx
Worked like Charm :)
PS: Feel so happy !!
john
Hello Thank you for this great tutorial
i followed your guide but in step 7 when i try to create a user this i get this error
ERROR! Received 400 Bad Request
Shared secret registration is not enabled
i did change
#Enable registration for new users.
#
enable_registration: true
but the issue still the same
please help
Janne Ruostemaa
Hi John, thanks for the question. The default configuration only allows registrations locally or using the shared secret, by enabling registration, anyone can create an account on your Riot server if they know the server URL. Since you’ve enabled registration, you could test creating an account using the Riot web app by selecting the ‘Advanced’ option and entering your Matrix server URL.
Joaquim Homrighausen
The pre-built packages now work quite well for installing Synapse. Also, if you proxy Synapse using nginx for 8448, and you’re not worried about “local eavesdropping”, you should be able to keep most/all of LE/TLS handling out of Synapse.
Sam
Thanks for the tutorial, could you please tell me how to log into matrix admin panel?
i tried the url URL http://example1.com:8008, but it did not work. I would like to change few settings, for eg: disabling room creation by normal users, i see that riot don’t have option for that.
Thanks
Janne Ruostemaa
Hi there, thanks for the question. The example.com URLs are just that, examples. You’d need to replace it with your own domain or use your cloud server’s IP address if you do not have a domain at hand. As for the user permissions, you need to disallow users from publishing rooms on your server by editing the room_list_publication_rules in your homeserver.yaml file.
alex
Thanks a lot this is a great guide, and the only one that just worked for me on Ubuntu 18.04.
Felix
Thank your for this guide! That’s the first one that worked for me!
There’s just one thing that I cannot get over:
how do I start the synapse server on reboot? I don’t find a way to implement this
cd ~/synapse
source env/bin/activate
synctl start
into a crontab of any sort. There’s also no service installed that I could activate in systemctl.
Do you have a solution for this?
Thanks!
Janne Ruostemaa
Hi Felix, thanks for the question. Matrix doesn’t currently come with a service file itself, but other users have contributed one to their GitHub repository. Have a look at the systemd service provided here. Note that you’ll need to set the User, WorkingDirectory and ExecStart parameters to match where you installed Matrix.
Once you have the /etc/systemd/system/matrix-synapse.service created, reload the systemd daemon with sudo systemctl daemon-reload and start the service sudo systemctl start matrix-synapse
Don’t forget to stop the server if it’s already running:
cd ~/synapse
source env/bin/activate
synctl stop
Abhishek Cherath
How would I go about adding a TURN server to this setup? https://github.com/matrix-org/synapse/blob/master/docs/turn-howto.md
I found this, but it doesn’t say anything about how the dns records are to be configured, or which IP ports to open, which is confusing me.
Janne Ruostemaa
Hi Abhishek, thanks for the question. We don’t have a tutorial on TURN at this time but the how-to guide you linked seems fairly straightforward. If you are installing TURN on a separate server from your Matrix Synapse, you’ll need to point your Matrix server to it, for example, by creating DNS records for the TURN server IP address. Also according to the example configuration, it uses the port 3478 for both UDP and TCP so make sure those are allowed on both TURN and Matrix servers.
turn_uris: [ "turn:turn.matrix.org:3478?transport=udp", "turn:turn.matrix.org:3478?transport=tcp" ]
Gaurav
Hi Janne,
We followed all the steps and were able to establish matrix server. When we were doing security testing on this server, we have found https://riot.im/app/#/login page takes our server address and does the authentication. Chat rooms are created and then VC will start But in case we shut down the server, VC was still continue. Then we found out that even if we created rooms in our server and were doing VC in our server, still link created for VC was of PUBLIC server. For example links to our VC servers were like: https://jitsi.riot.im/. So VC server and VC was done using public Server always?? Can we make any configuration change to make sure it take only our establish server for VC.
Janne Ruostemaa
Hi there, thanks for the question. There’s a couple of things you might want to change if you wish to secure your Matrix homeserver for private use. The basic installation does not include a VoIP server, which means any video calls are routed through Riot’s own services as you noticed. You can install your own TURN VoIP server by following their how-to guide. You should also disable the trusted identification servers, trusted_third_party_id_servers in your homeserver.yaml file to only allow your own users to log in. This is due to how Matrix stores conversation history on all homeservers whose users are participating in a given room.
Anuja
Can you help me to answer in following questions:
1. Maximum no. of clients/ participants supported (without any performance issues)
2. Max. no. of simultaneous group meetings
3. Scalability & Load balancing
4. Minimum Hardware capability required for server for handling 50 users
5. Video call setup work-flow for better understanding
Janne Ruostemaa
Hi Anuja, thanks for the questions. Matrix homeserver is quite lightweight and does not require heavy investments in terms of server resources. Our $10 plan with 1 CPU and 2 GB RAM should be a good starting point for 50 users and can be quickly scaled up if need be. Load balancing should also be possible thanks to the Matrix federation but might require some extra attention to how users are registered. There are no fixed limits to simultaneous calls but installing your own TURN server will allow you to manage concurrent connections per user and the total per server.
anuja
As u suggested to set up the TURN server at “homeserver” in your earlier reply, my team worked the same. But we are failed as a riot client could not able to connect the identity server and “home server” to manage video calls. Currently, all calls are getting managed by “jitsi” server URL “https://jitsi.riot.im/JitsiConferenceGapingPrimoAni mal”.
Please help to setup “homeserver” as identity & Turn server both. I want to secure VC that all calls should be managed by my private network.
Thanks
Anuja
Please help how to test that our setting for the “TURN VoIP server” is done successfully. Is there a need to update setting at client end also so that it should connect with our home server as VoIP server in the complete conference? Currently, I am using Riot.im as a client to connect with our home server. Please guide.
Anuja
Can I replace “turn.matrix.org” with homeserver IP address?
like :
1. turn_uris: [ “turn:https://:3478?transport=udp“, :3478?transport=tcp” ]
2. releam : :
As I do not have domain name for home server public IP.
Please guide
Janne Ruostemaa
It might be possible to configure TURN using the server IP. However, Matrix requires TLS to be enabled which requires a valid domain name for your homeserver.
Janne Ruostemaa
You were likely unable to log in to your homeserver via the Riot client if your Matrix server has not been configured to use TLS with a trusted certificate. You’ll need to have a valid domain name for which you can have, for example, Let’s Encrypt issue an SSL certificate.
Janne Ruostemaa
Using your own TURN server should not need any extra steps on the client-side. We don’t currently have a detailed guide on TURN server but might look into putting on together. Until then, I’d recommend checking the TURN GitHub repository and issue tracker for more information.
Grui
perfect guide, everything is clear, detailed, working fine on a raspberry A+ !
Sanyo
Thank You for this great Tutorial!
I installed and configured all of your steps on a Debian System with Dynamic DNS, everything seems to be ok, but step 8 Logging into Matrix failed with domain url or server’s IP address
Browser with https:
502 Bad Gateway
nginx/1.14.2
RiotWebApp with https https://riot.im/app/#/login:
Server not available
—
Browser with http:
Welcome to nginx!
RiotWebApp with http https://riot.im/app/#/login:
Server not available
Do you know maybe what to do…?
Janne Ruostemaa
Hi there, thanks for the question. It sounds like you have the default config still active which is overriding your reverse proxy config. On your version of Nginx, you need to delete placeholder with rm /etc/nginx/sites-enabled/default , then systemctl reload nginx . Afterwards, open your domain on a web browser and you should see the Matrix page and be able to connect using the Riot client.
Sanyo
Thank you very much for your answer. As described by you, i proceeded as described, default remove and reloaded nginx and system reboot -> /etc/nginx/sites-enabled/default is now removed clearly. Unfortunately, this did not change anything… I hope that you can help me out :-)
sudo nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
Janne Ruostemaa
Ok, if the default config wasn’t the issue, I’d recommend checking that your reverse proxy /etc/nginx/conf.d/matrix.conf was saved and contains the all the necessary instructions as described in the reverse proxy section. You should also check that synapse is running by trying to start it again with synctl start.
Anders
HI,
How does my domain know to point to this server, am I setting up any dns records for upcloud? Or am I just pointing my domain or possibly subdomain to the ip address with a A record? Thanks
Janne Ruostemaa
Hi Anders, thanks for the question. You are right, you’ll need to create an A record to point your domain or subdomain to the public IP address of your cloud server. The actual steps for how this is done depends on your domain registrar, most of whom provide instructions for their service.
Alper Tayfun
Hello ,
I just installed matrix and synapse now.
I just running this :
register_new_matrix_user -c homeserver.yaml http://localhost:8008
Centos 7 – no tls configured – no running firewall
I got this error :
requests.exceptions.ConnectionError: HTTPConnectionPool(host=’localhost’, port=8008): Max retries exceeded with url: /_matrix/client/r0/admin/register (Caused by NewConnectionError(‘: Failed to establish a new connection: [Errno 111] Connection refused’,))
What can I do ?
When I started synapse :
started synapse.app.homeserver(‘homeserver.yaml’)
Janne Ruostemaa
Hi there, thanks for the question. The error message you got would indicate that something is blocking the connection. While you did mention that you don’t use a firewall, CentOS 7 usually comes with firewalld enabled by default. I’d check that with firewall-cmd --list-all just to be sure. Also, check that Synapse is listening to the localhost at port 8008 in your homeserver.yaml e.g.
- port: 8008 tls: false bind_addresses: ['127.0.0.1']Anders
I am not quite sure what I am doing wrong I have the following service config
User=root
Group=nogroup
WorkingDirectory=/root/synapse
ExecStart=/root/synapse/env/bin/python -m synapse.app.homeserver –config-path=/root/synapse/homeserver.yaml
SyslogIdentifier=matrix-synapse
But I get the following errors when I try to stop and start.
When I pwd inside my synapse folder install its `/root/synapse`
root@kitson-chat:~/synapse# systemctl status matrix-synapse.service
* matrix-synapse.service – Synapse Matrix homeserver
Loaded: loaded (/etc/systemd/system/matrix-synapse.service; disabled; vendor preset: enabled)
Active: failed (Result: exit-code) since Sun 2020-08-02 19:05:59 UTC; 22s ago
Process: 21867 ExecStart=/root/synapse/env/bin/python -m synapse.app.homeserver –config-path=/root/synapse/homeserver.yaml (code=exited, status=1/FAILURE)
Main PID: 21867 (code=exited, status=1/FAILURE)
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: self.stale_possible_simple_keys()
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: File “/root/synapse/env/lib/python3.6/site-packages/yaml/scanner.py”, line 292, in stale_possible_simple_keys
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: “could not find expected ‘:'”, self.get_mark())
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: yaml.scanner.ScannerError: while scanning a simple key
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: in “/root/synapse/homeserver.yaml”, line 1384, column 3
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: could not find expected ‘:’
Aug 02 19:05:58 kitson-chat matrix-synapse[21867]: in “/root/synapse/homeserver.yaml”, line 1385, column 1
Aug 02 19:05:59 kitson-chat systemd[1]: matrix-synapse.service: Main process exited, code=exited, status=1/FAILURE
Aug 02 19:05:59 kitson-chat systemd[1]: matrix-synapse.service: Failed with result ‘exit-code’.
Aug 02 19:05:59 kitson-chat systemd[1]: Failed to start Synapse Matrix homeserver.
Anders
got it working all good
Lallogo
I have this problem. Please i need help to resolve it.
Janne Ruostemaa
Hi there, thanks for the comment. If you are getting the same error message as above, the problem is in the homeserver.yaml file. Check the error output to find out where in the file the error is, e.g.
was missing a separator character “:” indicated by the following line:
theo
thanks! It works
bilalbilalsheikh
unable to call on different network?
Janne Ruostemaa
Hi there, thanks for the question. For calls to work between networks, your Matrix homeserver needs to be able to connect to other servers. You can check this with their federation tester. Additionally, you need to have configured a TURN server. The tutorial includes some troubleshooting steps you should try if your calls are not connecting.
YJ
I have installed and configured synapse server. All good. I was able to create users too. I am able ti login from Element client using the user credentials that I created.
It store all the data in the sqlite3 database and the filename is “homeserver.db”
My question is “How to access homeserver.db using sqlite on my linux “.
Where is my sqlite3
Janne Ruostemaa
Hi there, thanks for the question. The database is stored by default in your synapse directory. You should be able to open the database using the following command:
k3tan
Is there a way to auto start the “synctl start” on boot of machine?
Janne Ruostemaa
Hi there, thanks for the question. The Matrix default install from the source doesn’t include a service unit file but you can make your own. If you installed the Matrix home server in /root/synapse directory, create the following file in /etc/systemd/system/synapse.service
Then reload the systemd, start and enable synapse service.
Hannah
If you are trying to do this more recently, and using Ubuntu 20.04, you will need to change a couple things in the first section for installing prerequisites:
python3-pip
AND
python3-virtualenv
were the two that failed for me. Hope that helps someone
Janne Ruostemaa
Hi Hannah, thanks for the comment and pointing out the different package names for Ubuntu 20, we’ve updated the guide to include the changes.
GodGoldfish
Hi,
Sometimes some files can’t be sent :
(Access to XMLHttpRequest at ‘https://MATRIX.EXEMPLE.ORG/_matrix/media/r0/upload’ from origin ‘https://app.element.io’ has been blocked by CORS policy: No ‘Access-Control-Allow-Origin’ header is present on the requested resource.
http-api.js:332 POST https://MATRIX.EXEMPLE.ORG/_matrix/media/r0/upload net::ERR_FAILED)
Janne Ruostemaa
Hi there, thanks for the comment. It would seem that the error isn’t directly related to the Matrix network but rather a browser-side issue.
Kolby Wilson
Hi, I’m having issues connecting to other servers. When trying to connect to matrix.org from my homeserver it says 401: Unauthorized.
Could this perhaps be due to the SSL configuration with the reverse proxy?
Janne Ruostemaa
Hi Kolby, thanks for the question. SSL secured connections can be tricky to configure at times. I’d suggest double-checking the certificates are accessible to Matrix and that the time on the server is running accurately.
Andrew Evans
I am trying to follow these steps but when i finish, i am getting a too many redirects alert and i can’t seem to access.
Janne Ruostemaa
Hi Andrew, thanks for the comment. If you are seeing a redirection loop, it’s likely due to a misconfiguration in your reverse proxy setup. Check that your proxy_pass http://localhost:8008; is set to localhost as shown as opposed to the domain name of your Matrix server.
Tobias
Excellent! Thank you
Robert
Hi there. I’m getting an error while I am running the command :
(env) pi@piServer:~/synapse $ synctl start
Error in configuration at ‘signing_key’:
Error accessing file ‘CONFDIR/SERVERNAME.signing.key’:
[Errno 2] No such file or directory: ‘CONFDIR/SERVERNAME.signing.key’
synapse.app.homeserver(homeserver.yaml) failed to start (exit code: 1). Check the Synapse logfile, or run synctl with –no-daemonize.
Do you have any idea why?
Thanks !
Janne Ruostemaa
Hi Robert, thanks for the comment. Matrix doesn’t seem to be able to find your message signing key in the defined location. You could try regenerating the homeserver.yaml to see if that’ll fix the issue.
gm
i have the same problem, and how i can add admin user, and when i enable registration still i cannot add user(using riotapp)
Janne Ruostemaa
Hi there, thanks for the comment. You can add admin users on the command-line as described in the tutorial, just make sure you are within the Synapse virtual environment and using the right homeserver.yaml file. As for enabling registrations, remember to restart the synapse service to apply any changes to your homeserver.yaml file, after that it should work just fine.
mahe4
you didn’t really answer to the problem.
i also get
ERROR! Received 400 Bad Request
Shared secret registration is not enabled
when i try to add a user.
how do i solve that problem?
Janne Ruostemaa
Hi there, thanks for the comment. Unfortunately, we’re unable to reproduce the error and would need to know more about how you came to the issue to be able to respond more accurately.
dev
hi
how to get synapse list of users
Janne Ruostemaa
Hi there, thanks for the question. Your Matrix data is saved in the /home/synapse/homeserver.db file which you can open with the sqlite client installed along with the rest of the prerequisites. Then list the usernames with the command below.
Goran
Well, such a great list of instructions on how to setup your Matrix Home server. I went through and had no issues in setting up the server. Could you be so kind to give me two commands.
List users
Delete users
What I am saying is, do I need to go through sqlite client?
Once again from so many instructions how to install the homeserver on the web, this was by far the best I found. And with my really limited knowledge it took me only half an hour
Samir Haliru
Hi there. While it is possible to use sqlite for listing users, the recommended approach for administering users on your Synapse homeserver is with the Admin API. The links below describe how to list and delete users:
List users: https://matrix-org.github.io/synapse/latest/admin_api/user_admin_api.html#list-accounts
delete users: https://matrix-org.github.io/synapse/latest/admin_api/user_admin_api.html#deactivate-account
There is also a project on GitHub which provides an admin panel for managing users and rooms if that interests you: https://github.com/Awesome-Technologies/synapse-admin
SparrowM
Hi! I followed your tutorial, matrix is accessible. But it wont show up on domain name, its rather showing up on VPS’s I.P address. what could be the issue?
Domain was newly purchased while I was using your tutorial and I used the main domain, i did not use any sub domain like you used matrix.example.com – I used mydomain.com
Janne Ruostemaa
Hi there, thanks for the question. Did you set your domain A record to point to your Matrix Homeserver’s IP address? How this is done will depend on your domain registrar but we’ve got some general guidelines of DNS records you can check to figure it out.
hadi
can anybody me tell me how to run this command in correct way
python -m synapse.app.homeserver
portal.osmani.com:8448
homeserver.yaml
generate-config
report-stats=no
Janne Ruostemaa
Hi Hadi, thanks for the question. I’m assuming you want to run the startup-config in a single command. Based on these, the following should work:
sigma
I also implemented coturn with this server and is working. It still have a lot of issues like online user, no notifications, sometimes you can’t make a call and so on.
Kim
How do I configure this installation to use an external PG database?
Janne Ruostemaa
Hi Kim, thanks for the question. Matrix has instructions on this in their GitHub documentation